SSH (Secure Shell) is a protocol used to connect securely to a remote container and execute the required commands on it. SSH commands are encrypted and secure: client/server connection is authenticated using a digital certificate, and passwords are protected by being encrypted.
To make SSH access available in CloudJiffy, a new infrastructure component was added to the core - SSH Gate. SSH Gate accepts users’ connections from the internet and then transmits these connections to the desired container, using an internal network.
The authentication procedure in CloudJiffy SSH Gate is divided into two independent parts:- the connection from the end user to Gate (external authentication)
-
the connection from Gate to users’ container (internal authentication)
Both parts of the authentication procedure are based on a standard SSH protocol, using public/private keypairs.
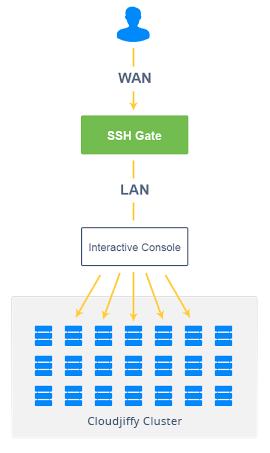
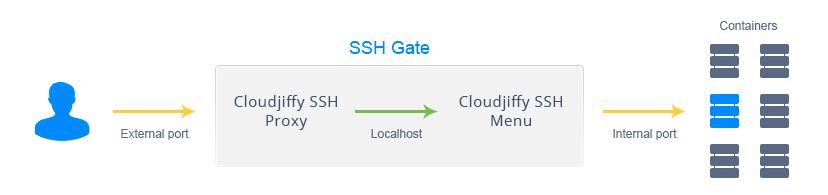
- The whole account where you can navigate across your environments and containers using an interactive menu without extra authentication
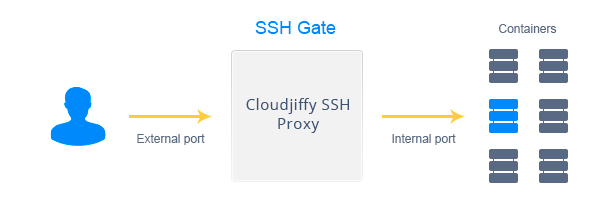
-
Separate containers directly while working with them remotely via additional tools (e.g. Capistrano) or using SFTP and FISH protocols.
sudo /etc/init.d/jetty start
sudo /etc/init.d/mysql stop
sudo /etc/init.d/tomcat restart
sudo /etc/init.d/memcached status
sudo /etc/init.d/mongod reload
sudo /etc/init.d/nginx upgrade
sudo /etc/init.d/httpd help
In addition, we provide support of SFTP (Secure File Transfer Protocol) by implementing the threaded daemon for SFTP connections processing. It lets you access, manage and transfer files directly to the container via SSH gate, and in such a way, ensures data security.
An additional secure network protocol is FISH (Files transferred over Shell protocol). It is supported by a number of popular FTP-clients and file managers (e.g. Midnight Commander, Konqueror, lftp, Krusader, etc) and permits a user to securely access and manage a container’s file system.